#What Is A Network Security Key? How To Find It?
#What Exactly Is a Network Security Key?
A network security key is an alphanumeric key that one enters as authorization to gain access to a local area network. In simple terms, it is your WiFi password.
A network security key is responsible for establishing a secure connection between the network and the user requesting the access (via a wireless device). It protects the network and all connected equipment from unwanted access.
The security key can also be a passphrase in the form of a digital signature or biometric data used for providing authorized access. It is widely used in common services, such as online shopping, money transactions (in the form of OTP), online banking, and logging into an email account or any network device.
Why Is It Important?
There are several benefits of using a network security key:
- It ensures that the whole network and connected devices are secure
- It provides security information of devices associated with the network.
- It allows you to protect the personal data of clients connected to the network
- It prevents virus and spyware attacks from the internet.
All in all, it helps you protect the usability, safety, and reliability of network and data while providing authentication and access control for resources.
Different Types Of Network Security Keys
Wired Equivalent Privacy (WEP)
WEP was introduced in 1997 to provide a level of security comparable to that of a traditional wired network. It is recognizable by its key of 10 or 26 hexadecimal digits.
The wireless network uses radio waves to transmit data all over an area within its range. To make this data secure from unauthorized devices, WEP adds a layer of security to the wireless network. This is usually done by adding strong encryption to the data. Devices that are authorized on the network will be able to decrypt the data and successfully conduct inner communications.
WEP became a WiFi security standard in 1999, and within a couple of years, 256-bit (more secure) WEP was released. However, 128-bit remains the most common version of WEP implementations.
Despite the increased key size and several revisions of the protocols, many security flaws were discovered in the WEP standard over time. As CPUs got more powerful, it became simpler to exploit those flaws. A few proofs-of-concept were developed in early 2001.
By 2004, WEP became highly vulnerable and unreliable, so WiFi Alliance decided to retire all WEP implementations. In 2005, the FBI managed to crack WEP passwords in minutes using freely available tools.
WiFi Protected Access (WPA)
WPA was developed by WiFi Alliance to deal with the limitations of WEP. It became available in 2003, a year before WEP was officially retired. It uses 256-bit encryption keys to secure data.
The two major changes implemented with WPA include
- Temporal Key Integrity Protocol (TKIP): it dynamically creates a new 128-bit key for each packet, preventing the kinds of attacks on the compromised WEP.
- Message Integrity Check: it prevents attackers from altering and resending data packets.
WPA also implements the Extensible Authentication Protocol (EAP) for authorizing users. It can use various methods to verify each device’s identity instead of authorizing the device based solely on its MAC address.
Firmware updates that allow both client and server machines to implement WPA became widely available during 2003. However, like its predecessor (WEP), WPA has been demonstrated to be vulnerable to intrusion via both proof-of-concept and applied methods.
WiFi Protected Access 2 (WPA2)
The second version of WPA was released in 2004. It supports Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP), an AES-based encryption protocol designed for Wireless LAN.
It was developed to address the vulnerabilities presented by the WPA. It is much more secure than WEP and TKIP of WPA. TKIP is still included in WPA2 as a fallback protocol for interoperability with WPA.
CCMP provides three security services: Data confidentiality, Authentication, and Access Control in conjunction with layer management. WPA2 is still not completely secure, especially on public wireless networks.
In 2017, security researchers revealed high-severity vulnerabilities in WPA2 that could allow attackers to eavesdrop on WiFi traffic passing between routers and connected devices. More specifically, attackers can use a novel technique called Key Reinstallation Attacks (KRACKs) to read data that was previously assumed to be safely encrypted.
Based on the network configuration, one could inject malware into websites or manipulate data. Although vendors have already made patches and updates available to the public, it is not impossible for invaders to exploit WPA2 vulnerabilities using state-of-the-art computer technology.
WiFi Protected Access 3 (WPA3)
In 2018, WiFi Alliance released WPA3 with numerous security enhancements over WPA2. It has two deployment modes: WPA3-Personal and WPA3-Enterprise. The former offers more individualized encryption options, while the latter improves cryptographic strength for networks transmitting sensitive information.
The Personal mode still mandates the use of CCMP-128 as the lowest-level encryption algorithm and the Enterprise mode uses an equivalent 192-bit cryptographic strength.
WPA3 simplifies the process of pairing WiFi devices (such as IoT devices) without graphical user interfaces. It also provides seamless encryption on open WiFi hotspot networks and mitigates security issues posed by weak passwords.
However, widespread adoption of this new standard won’t happen overnight. Some manufactures have started offering software updates with the WPA3 capability in existing products, but there is no guarantee. Since some WPA3 functionality requires hardware updates, it may take years for businesses and consumers to upgrade.
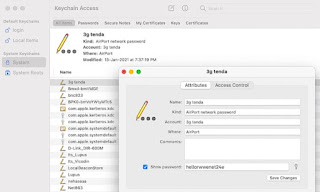
How To Find Network Security Key?
Typically, all routers contain a label that lists the Wireless Network Name (also called SSID, short for Service Set Identifier) and Password, which is a combination of alphanumeric characters (for example, HG2HG242eb73).
If your device is connected to the router, you can easily find the network security key by going to the settings. Just follow these steps —





0 Comments